Building Device-Aware Sessions in a JWT-Based Auth System
How JWT-Based Auth Systems Can Track Devices and Revoke Access with Precision
JWTs (JSON Web Tokens) have become the go-to solution for modern authentication systems — and for good reason. They’re compact, stateless, and easily verifiable on the server without hitting a database. This design unlocks a great deal of performance and scalability, especially for APIs serving mobile or frontend-heavy applications.
But this convenience comes with a silent cost.
Imagine a user logs into your app from multiple devices — their phone, a laptop, and perhaps a tablet. A few days later, they misplace their phone. Naturally, they’d like to revoke access from that device while maintaining their sessions on the others. With traditional server-based session auth, this is relatively straightforward.
But in a stateless JWT setup, the backend has no concept of which device issued which token. Once a token is signed and handed over, it remains valid until it expires, unless you implement a custom revocation mechanism.
This is the crux of the problem: JWTs are stateless, and by extension, blind. They don’t keep track of device-specific sessions, and they don’t offer built-in ways to revoke or inspect individual tokens once issued. This becomes a major limitation when building for real-world use cases where users expect visibility and control over their sessions — the kind offered by platforms like Gmail, Facebook, or Spotify.
Stateless Doesn’t Mean Dumb — If You Design It Right
So how do you keep the benefits of JWT-based auth while introducing smart, device-aware session tracking?
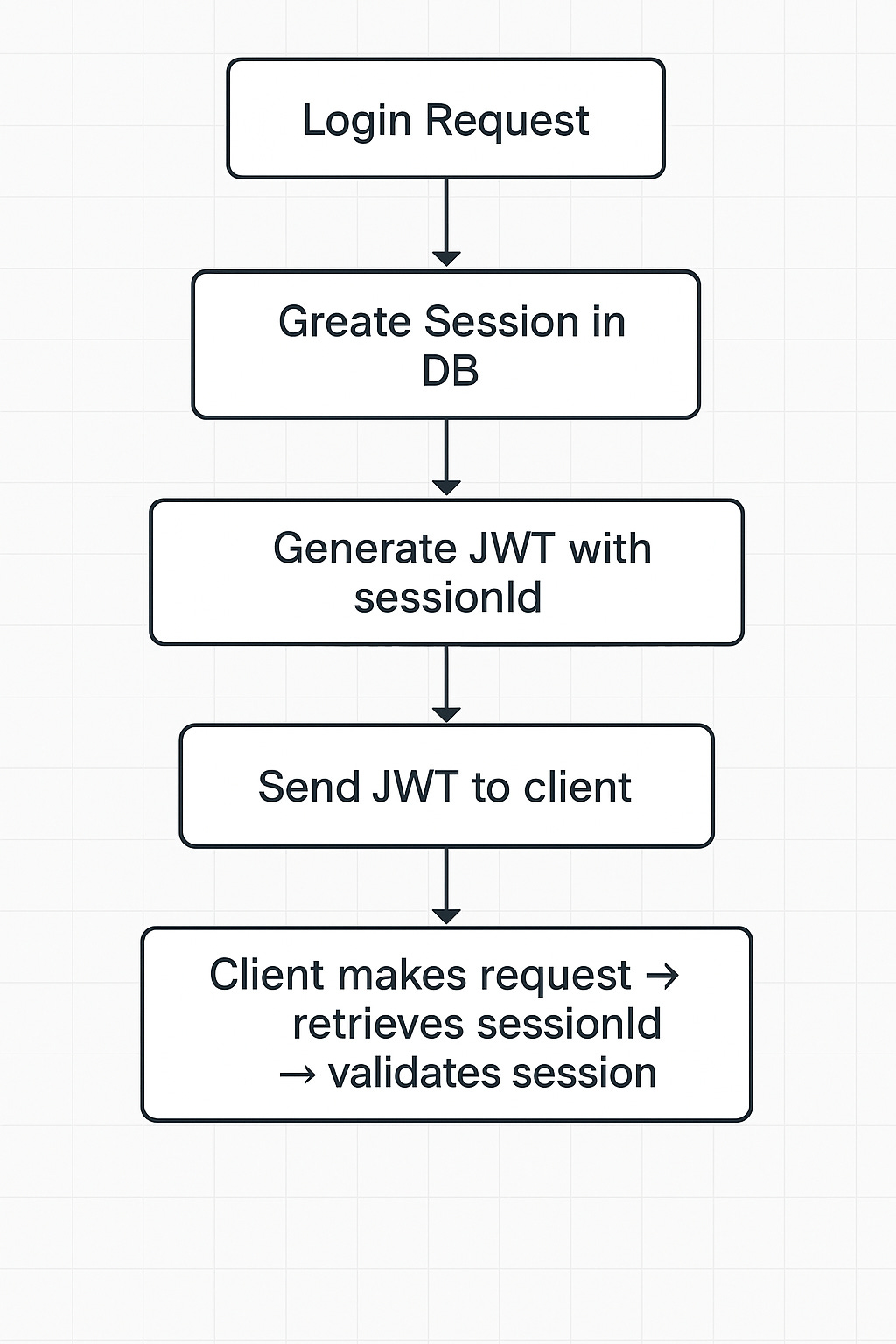
The key lies in augmenting your JWT flow with a persistent session layer. Instead of issuing a JWT and calling it a day, your backend creates a new session record every time a user logs in. This session is stored in a database or cache, and contains metadata about the login event — including the user’s IP address, device or browser fingerprint, geolocation (if applicable), and the timestamp of the login.
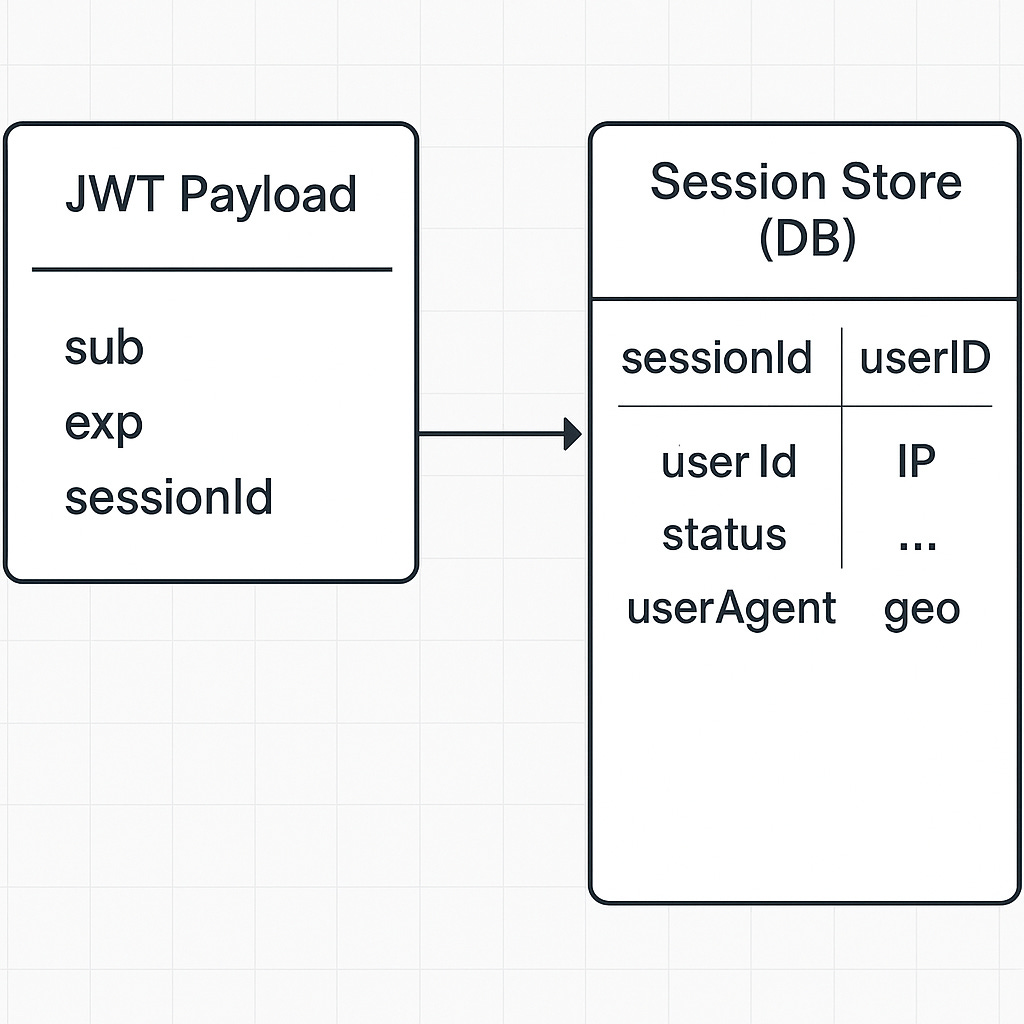
The JWT payload is then extended to include a unique sessionId — a reference to the corresponding session stored on the server. Now, every time a request is made, your middleware not only validates the JWT’s signature and expiry, but also checks whether the sessionId still points to an active session.
This changes everything.
With this small but crucial addition, your system now gains insight into who is logged in, from where, and on what device. It gains the ability to revoke sessions individually. It can flag anomalies, like logins from suspicious locations or multiple new devices within a short time frame. And it gives the user back control — allowing them to view their active sessions and terminate any of them on demand.
A Closer Look at Device-Aware Sessions
Let’s unpack this further. What does it actually mean to be “device-aware”?
In essence, it means that each login isn’t just treated as a generic access event, but rather as a distinct session tied to a device context. This device context can be inferred from the user-agent string, IP address, or even a client-generated fingerprint if you want stronger uniqueness.
Each session entry can look something like this:
{
"sessionId": "abc123",
"userId": "user-xyz",
"ip": "102.89.77.21",
"userAgent": "Mozilla/5.0 (Macintosh...)",
"device": "MacBook Pro",
"location": "Lagos, Nigeria",
"createdAt": "2025-07-18T09:30:00Z",
"expiresAt": "2025-08-18T09:30:00Z",
"revoked": false
}This record lives on the server (in Redis, MongoDB, PostgreSQL — your choice), and represents a real-world instance of an authenticated session. Unlike the JWT itself, which can only carry claims, this session store allows your system to update, revoke, extend, or inspect any login session.
And because every JWT includes the sessionId, you can now perform validation beyond just signature and expiry — you can enforce session revocation, check device legitimacy, or even enforce concurrency limits.
Why This Pattern Matters
You might be wondering: if JWTs are supposed to be stateless, doesn’t adding a session store reintroduce state and negate the benefits?
Not quite.
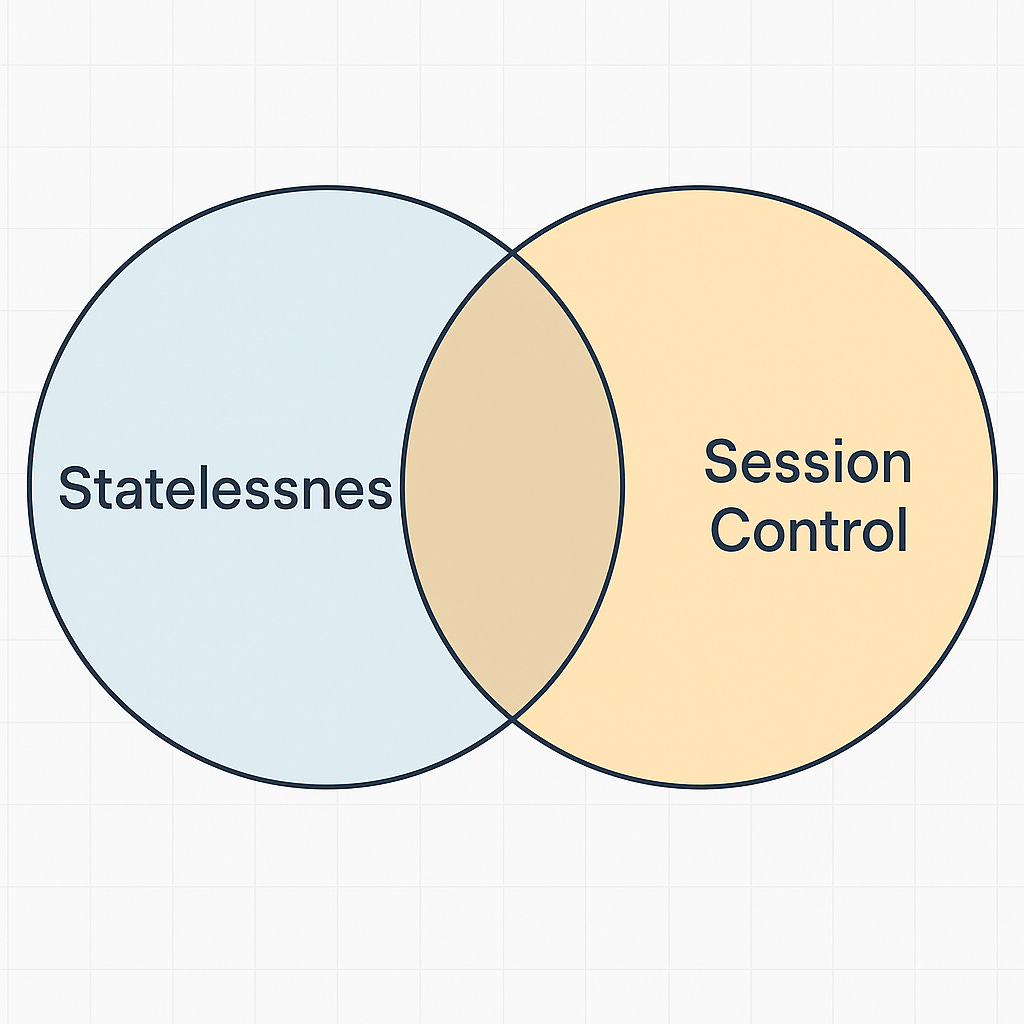
This pattern strikes a balance. The JWT still works as a compact, verifiable token that can be passed between services without frequent database lookups. But now, your system has the option to add context and control. You only need to query the session store when it matters — such as during sensitive actions or periodic session validation.
This hybrid approach gives you stateless performance most of the time, and stateful control when it counts.
From a user experience perspective, this is non-negotiable. Users expect to be able to log out of a device they no longer use. They expect to see their login history and receive alerts for suspicious logins. Without device-aware sessions, you’re unable to meet those expectations.
From a security standpoint, the benefits are even greater. You can:
Identify and revoke stolen tokens in real-time
Detect impossible travel (e.g., logins from Nigeria and Canada 2 minutes apart)
Escalate authentication requirements based on device reputation
These are powerful capabilities that require minimal overhead when implemented with care.
Building It Right
Implementing device-aware sessions requires a few architectural considerations.
First, your backend should create a new session record for every successful login. This includes metadata like the user-agent, IP address, and an expiration timestamp. This session is assigned a unique ID.
Second, your JWT payload should include this sessionId. It doesn’t need to carry any of the session data — just a reference to the session record on the server.
Third, your request pipeline should include middleware (or a guard) that checks:
Is the token’s signature valid?
Has the token expired?
Does the
sessionIdexist, and is it still active?
When a user logs out, you simply mark that session as revoked in the session store. You can either soft-delete it or add a revoked: true flag. Any subsequent requests with that sessionId will now fail, even if the token hasn’t technically expired.
This opens the door to richer features, like:
“Log out of all devices”
“Terminate this session”
Admin dashboards for tracking login patterns
Analytics on session lifespans and behavior
Final Thoughts
JWTs were never designed to handle sessions. But with the right patterns, you can extend them to do just that — and do it well.
Device-aware sessions bring together the best of both worlds: the performance and portability of JWTs, and the control and visibility of traditional session-based auth. In a world where users expect transparency and security, this isn’t just a nice-to-have — it’s a foundational layer of trust.
If you’re building an auth system from scratch or revisiting your current implementation, now is the perfect time to consider this pattern.
It’s lightweight. It scales. And most importantly, it gives your users the power they didn’t know they were missing.
👋 Before You Go
I’m considering turning this pattern into an open-source package for Node.js and NestJS — something drop-in, with support for session storage, revocation, device tracking, and optional admin views.
Would you use something like that?
Reply and let me know. Your feedback might help shape it.
Until next time,
Korede